When infected, your web browser will start misbehaving or freeze. When your browser is infected, you should scan the computer with an effective antivirus program for any malware or virus and take immediate action if the computer is infected. This is because it’s fairly common for corporate networks to enforce a rule which says that users may only run certain trusted applications. No code signature usually means your application is not trusted.
That’s because \RPC Control is not an enumerable file system location, so the vulnerable process would not be able to find \RPC Control\file1.txt via enumeration. Instead, we must start off by creating temp\folder1\file1.txt as a bona fide file, allowing the vulnerable process to find it through enumeration. Only afterward, just as the vulnerable process attempts to open the file for deletion, we turn temp\folder1 into a junction pointing into the object namespace. This will demonstrate the excellence of the program and its safety. After viewing the file, recovery occurs automatically without your effort.
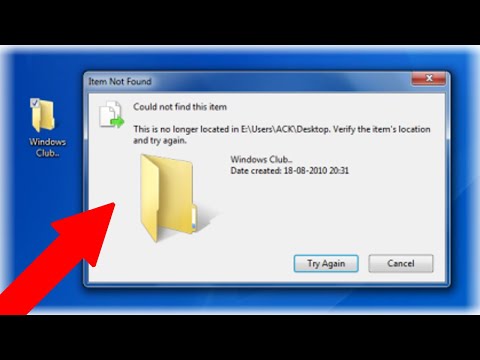
Messages Telling Why You Cannot Delete File
To check the reason and fix the problem of the DLL files missing, you can also use Windows system file checker. Using the WIN+R buttons on the keyboard and input “cmd” to open your system commander. Type “sfc /scannow” then hit enter, it may take several minutes to finish.
- Once you have downloaded your plugin, either run the installer , or copy the plugin files to a folder FL Studio can scan.
- After the software has been fully uninstalled, restart your PC and reinstall FL Studio software.
- S0598 P.A.S. Webshell P.A.S. Webshell can delete scripts from a subdirectory of /tmp after they are run.
- So .Exe is just the file extension for an executable file, which means it’s a file that can be run or executed by the computer.
Similarly, DLLs can undergo upgrades and also have version numbers. Having two interdependent component types that are each versioned separately over time can lead to complex run-time mismatches. If a method name in one of the components has changed, or the set of passed parameters is different, then the application either will not run or may crash when the problem call is made.
Suspect a file is incorrectly detected (a False Positive)?
ComRAT has also used a unique password to decrypt the file used for its hidden file system. S0344 Azorult Azorult uses driversol.com/dll an XOR key to decrypt content and uses Base64 to decode the C2 address. G0007 APT28 An APT28 macro uses the command certutil -decode to decode contents of a .txt file storing the base64 encoded payload. S0622 AppleSeed AppleSeed can decode its payload prior to execution. ID Name Description S0469 ABK ABK has the ability to decrypt AES encrypted payloads.
HP SmartFriend is a support service that can help you prevent and remove unwanted software on your computer. You can avoid computer problems including viruses, spam, and spyware by using simple safety precautions when you connect your computer to the Internet. You can begin using the following security actions immediately. HP recommends using the Windows Defender Offline scan if you suspect your computer is infected with malware or a virus.

